This post looks at two-factor authentication adoption in the wild, highlights the disparity of support between the various categories of websites, and illuminates how fragmented the two factor ecosystem is in terms of standard adoption.
Performing a longitudinal analysis highlights that the adoption rate of 2FA (two-factor authentication) has been mostly stagnant over the last five years, despite the ever increasing number of accounts hijacked due to the reuse of passwords found in data breaches and phishing attacks. Even more troublesome, looking at the type of 2FA offered reveals that some verticals, including some that have widely adopted 2FA, solely rely on custom two-factor solutions, instead of using two-factor standards, such as U2F/FIDO and TOTP.
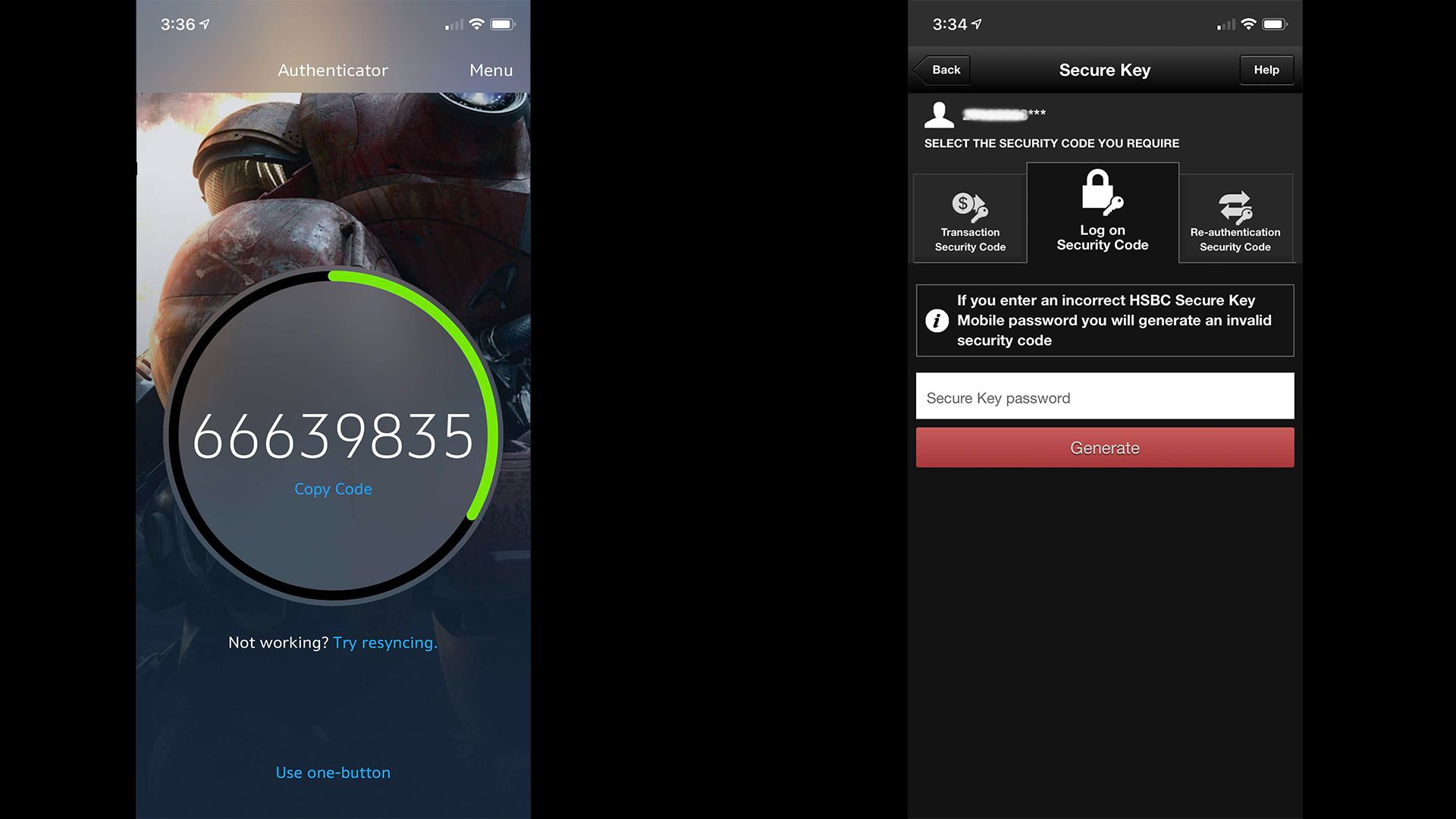
Arguably, this behavior should be considered harmful to Internet ecosystem security, as it tends to create an unhealthy competition between sites to entice users to use different systems and install many apps. For example, as you can see in the screenshot above, HSBC and Blizzard Entertainment rolled their own proprietary two-factor software that requires you to install their app. They also use their own lingo and workflow e.g HSBC ask for a PIN to generate the TOTP code and call their software authenticator a secure key which is confusing to say the least. These practices certainly does not make it easy for users who have to learn the quirks of each system they enroll to.
In contrast, if every site were to use standardized two factors and a common language, once the users have installed a single app or bought U2F hardware dongles, they would be able to use them everywhere with a consistent user experience. In that ideal world, every site supporting 2FA would benefit from a virtuous snowball effect and user life would be a lot easier.
The remainder of this blog post is organized as follows:
- Methodology: How the data was collected and what are the study limitations.
- 2FA prevalence: A summary of how widely deployed 2FA is across the ~1200 sites analyzed.
- Adoption rate: A look at 2FA adoption rate over the last five years.
- Adoption by vertical: Teasing apart 2FA adoption by industry vertical.
- Type of 2FA offers: A delve into what type of 2FA (software, SMS, hardware, etc.) are the most commonly offered.
- Standard adoption: How widely adopted U2F and TOTP are for the sites that are offering 2FA.
Before diving into the results, let me briefly describe how the data was collected and analyzed.
Methodology
To establish how many sites offers 2FA (two-factor authentication) and what kind of second factors are offered in the wild, I pulled the list of sites offering 2FA from dongleauth.info. To have historical perspective, I relied on the fact that the dongleauth.info git repo has been active since 2014 and pulled the list of sites as it was after the last git commit of each year from 2014 until 2017. Finally, I wrote a few python scripts to aggregate their yaml files and compute the statistics needed to create the charts that are used in this post (raw results available here).
Study limitations
Among the main limitations of this approach, it is obvious that it is not systematic - ideally, we would go through all of the top 1,000 sites and manually verify if 2FA is available and, if so, in which format and what language is used. Similarly, the examples used through this post are anecdotal: I didn’t do a formal analysis of the language used to describe 2FA across all sites. Finally, while there are a lot of studies that show consumers are picky on what app they install, there is no user research that directly shows that users are unwilling to install all the security app that are needed.
Study goal
That being said, this blog post is meant to be a conversation starter and raise awareness, rather than a full-blown research paper. In that context, I would argue that the data presented in this blog, which is used to support its claims, are good enough as the issues are so widespread that they are obvious whichever way you look at them. In particular, looking at the database coverage for the 2015 old version of Alexa top 1000 sites (the recent one can’t be downloaded since Amazon bought it) shows that the database covers 40% of the top 100 domains and 23% of the top 500 - this is not perfect, but it is more than enough to spot trends.
Future work
Moving forward, I agree that the community would benefit from a more rigorous study with clear recommendations that can be used as a reference by CISOs, CTOs, policy makers, and other key opinion formers. It is something that I hope we can do in 2019 - so, if you are interested in contributing, drop me a note!
With this out of the way, let’s delve into the study results.
How prevalent is 2FA authentication?
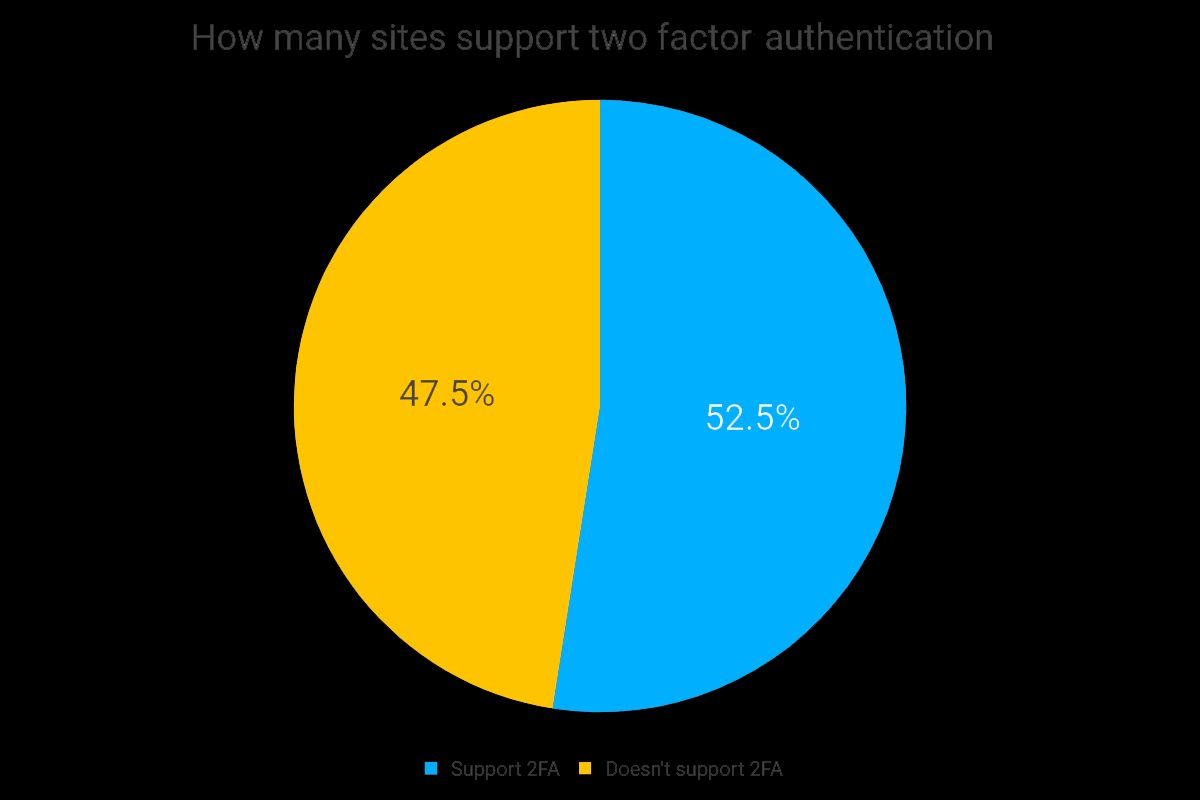
Overall, as of late 2018, 52.5% of the 1149 sites listed in the dongleauth database support 2FA. As we will see throughout this post, while having one site in two-supporting 2FA is good news, there is a lot of nuance behind this number that paints a somewhat grimmer picture.
Is 2FA adoption increasing?
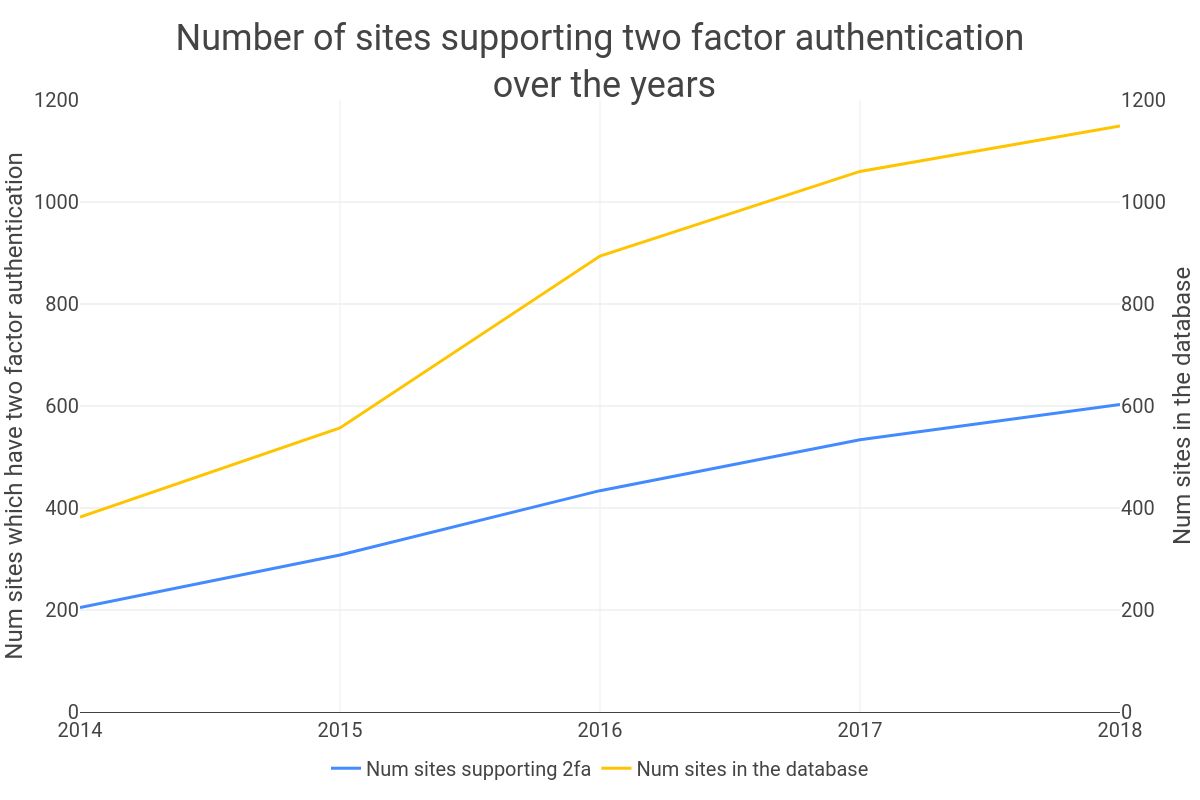
To evaluate if the adoption rate of 2FA is increasing, I plotted the number of sites in the database at the end of every year since its inception (2014) and how many of those sites were marked as supporting 2FA. The resulting chart, visible above, shows that the trends don’t look great, while the number of sites supporting 2FA grew from 205 in 2014 to 603 in 2018 during the same period, the total number of sites in the database growing from 382 to 1149. This means that the ratio of sites supporting 2FA barely changed over the last four years: the adoption rate was 53.66% back in 2014, 48% in 2016, and back above 50% in 2017 (50.38%)
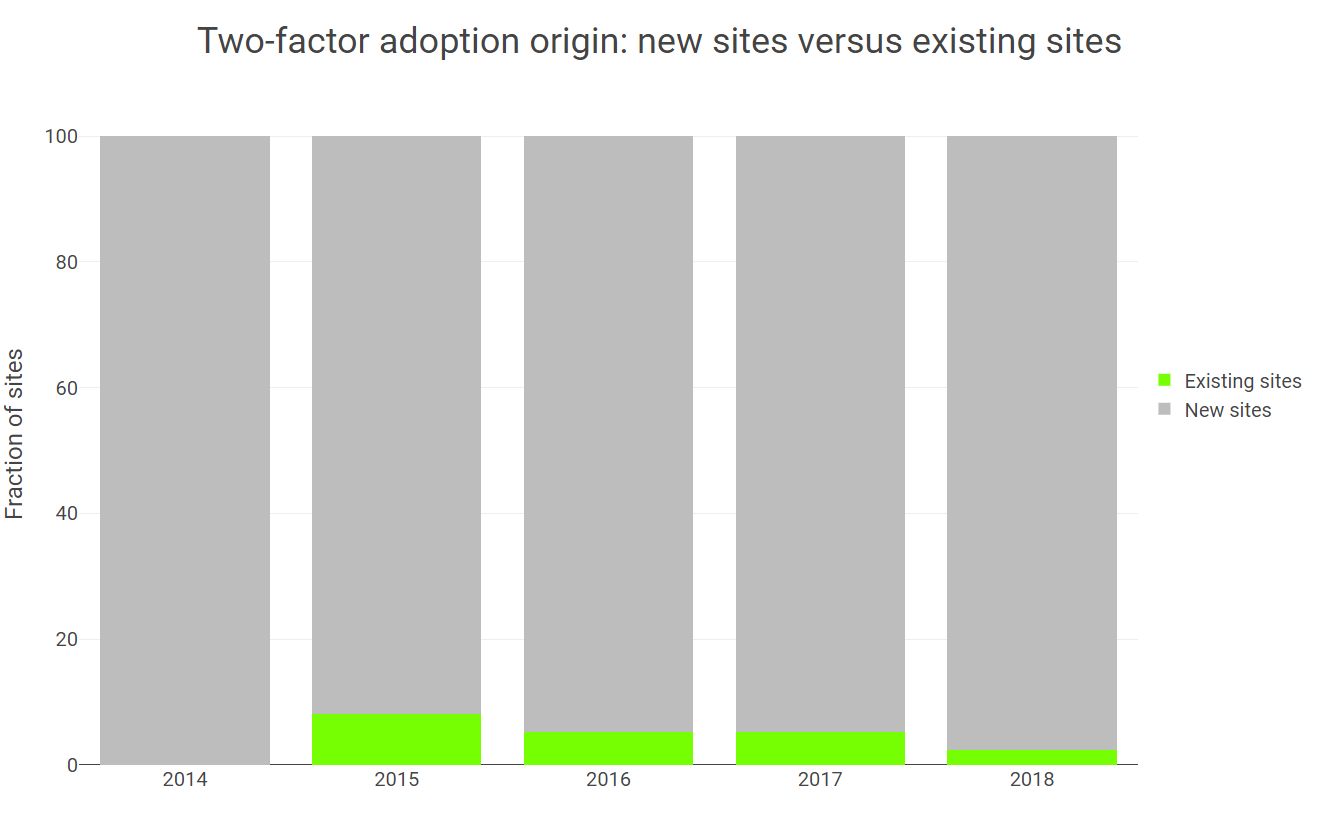
Now, one might argue that the main driver behind this stagnation is the fact that the dongleauth database grew by 300% over the last five years (~1200 up from 400) and that the newcomers are smaller/newer sites with less resources, which are, therefore, less likely to have 2FA. To test (and refute) this hypothesis,I looked at how much of the 2FA adoption growth was due to existing sites turning on 2FA. As visible in the chart above, turn out that very few sites that didn’t have 2FA from the get-go did adopt it after being added to the database. This leave us with the conclusion that:
Understanding why sites don’t adopt 2FA and what can be done to incentivize them to do so are key questions that need to be answered, so that we can devise an effective global strategy that will ensure a steady adoption.
Support for various categories
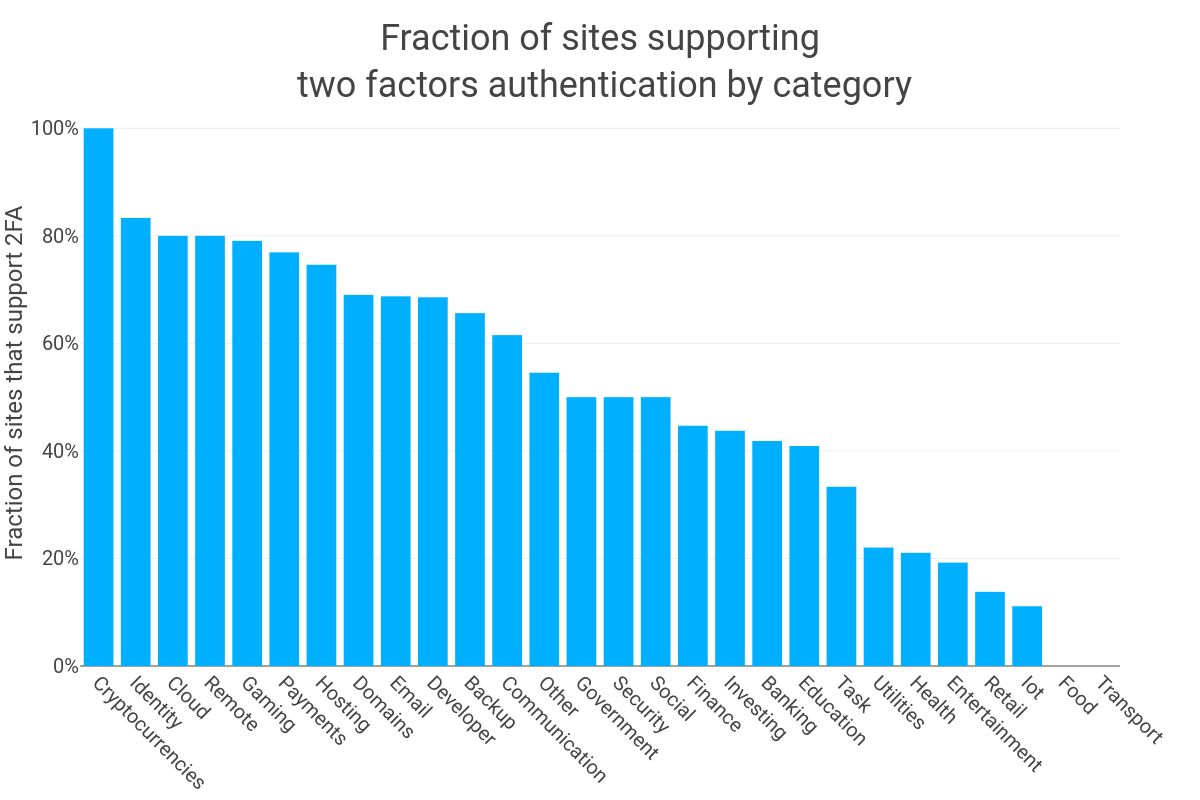
Looking at the adoption of 2FA by site categories reveals that FINTECH- (financial technologies) and IT (information technology)-related services, such as cryptocurrency and cloud services, are leading the 2FA adoption charge. The sites related to services that predated the Internet, such as utilities, food, and transports, unsurprisingly, have the lowest amount of adoption. The most concerning part of this breakdown is that a few categories of sites that handle very sensitive user data, such as education (40.9%) and health (21%), have a very low adoption rate. This highlights the need, as a community, to help those sites jump on the 2FA bandwagon to better protect their user data.
Type of second factor supported
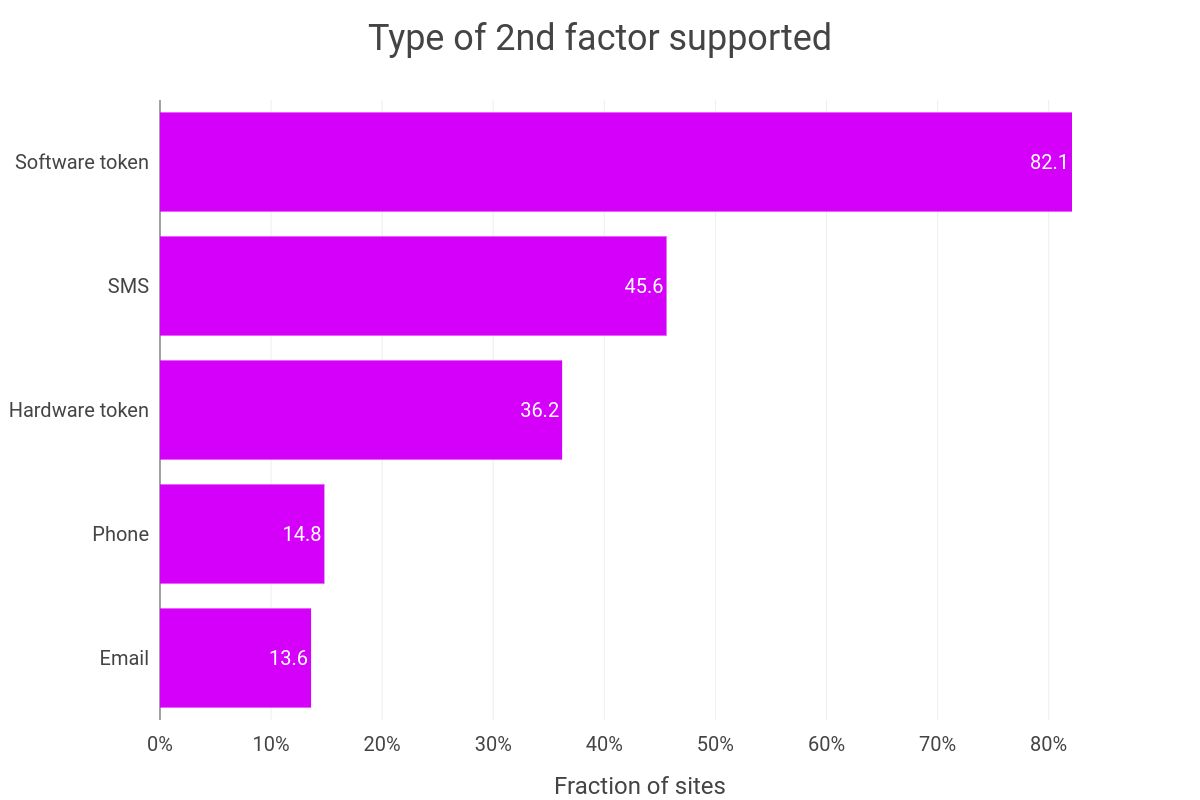
Looking at the type of 2FA supported across the board reveals that software based 2FA is by far the most widely supported second factor, with 82.1% of the sites supporting 2FA offering it. SMS, with 45.6%, is a distant second and hardware token is third, with only a 36.2% adoption rate. This breakdown is probably best explained by the fact that software-token systems are easier to implement and have no operational cost, whereas sending SMS/offering a hardware token does.

Obviously, the price argument is quickly becoming obsolete with the rise of the U2F hardware standard, as it allows any site to rely on security keys to do 2FA with a few lines of javascript. With webauthn and FIDO2 becoming mainstream in 2018, it will become easier than ever to offer a hardware 2FA. This is great news for user security, as U2F keys are the only type of second factor that can’t be phished, because the proof of ownership of the second factor is directly exchanged between the user key and the website.
The webauthn/FIDO2 standards will allow sites to offer unphishable hardware-based 2FA with just a few lines of javascripts.
However, all of this will only happen if sites indeed leverage standards and don’t invent their own version of second factors. This brings us to the last and probably most important part of the post, as it comes down to the future of 2FA: do websites follow standards?
2FA standard adoption
As I alluded to in the introduction, the key to getting more users to use 2FA is to have all sites offering two-factor options to be standardized. This would allow users to reuse their existing app and hardware tokens, instead of having sites competing to get users to install proprietary apps or buying single-site tokens (which is also bad for the planet).
The willingness of the industry to adopt standards is becoming even more crucial, as the next generation of hardware tokens FIDO2, which offer browser native UI, will hit the mainstream in 2019.
Before delving into adoption rate, let me briefly recap what standards exist and when they appeared, so that everyone is on the same page:
- Software token: The industry standard for software-based 2FA are HTOP (“HMAC based one time password”) and TOTP (“time-based one-time password”). HOTP was standardized in the RFC 4226 in 2005 and TOTP in RFC 6238 in 2011 almost 10 years ago. The security risk associated with both protocol is that users need to input the code themselves which makes it phishiable. This security risk and ease of use what the driving reason for creating a hardware-based standard that didn’t requires user to input anything just touch a trusted device.

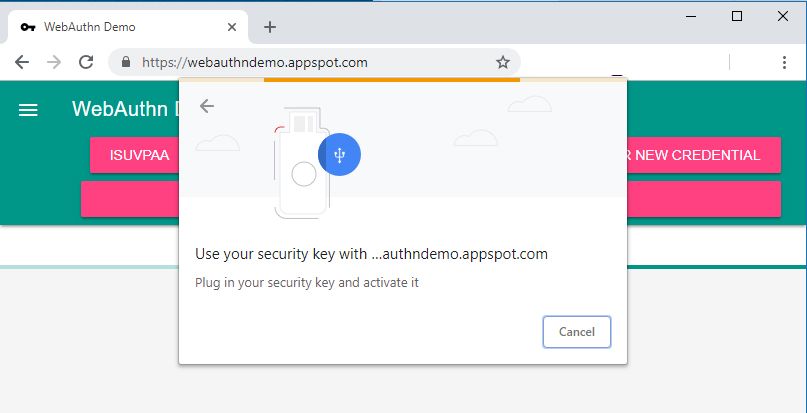
- Hardware token: The standard for hardware tokens created by Google and Yubico is called U2F(universal second factor) and was released by the FIDO alliance in 2015. Its successor FIDO 2 developpement started in 2016. The main difference between U2F and FIDO2 is that FIDO2 has both a protocol to talk to hardware devices (CTAP1) and a web API called webauthn that allows sites to use a native browser UI (as visible below) to prompt users to touch their key. Webauth is becoming mainstream with Chrome/Firefox/Edge support rolling out. You can test the native UI here.
Those standards, specially webauthn, offer the promise of a consistent user 2FA experience across the Internet, which, in the long run, is critical to having unphishiable accounts become the norm.
Standard overall adoption rate
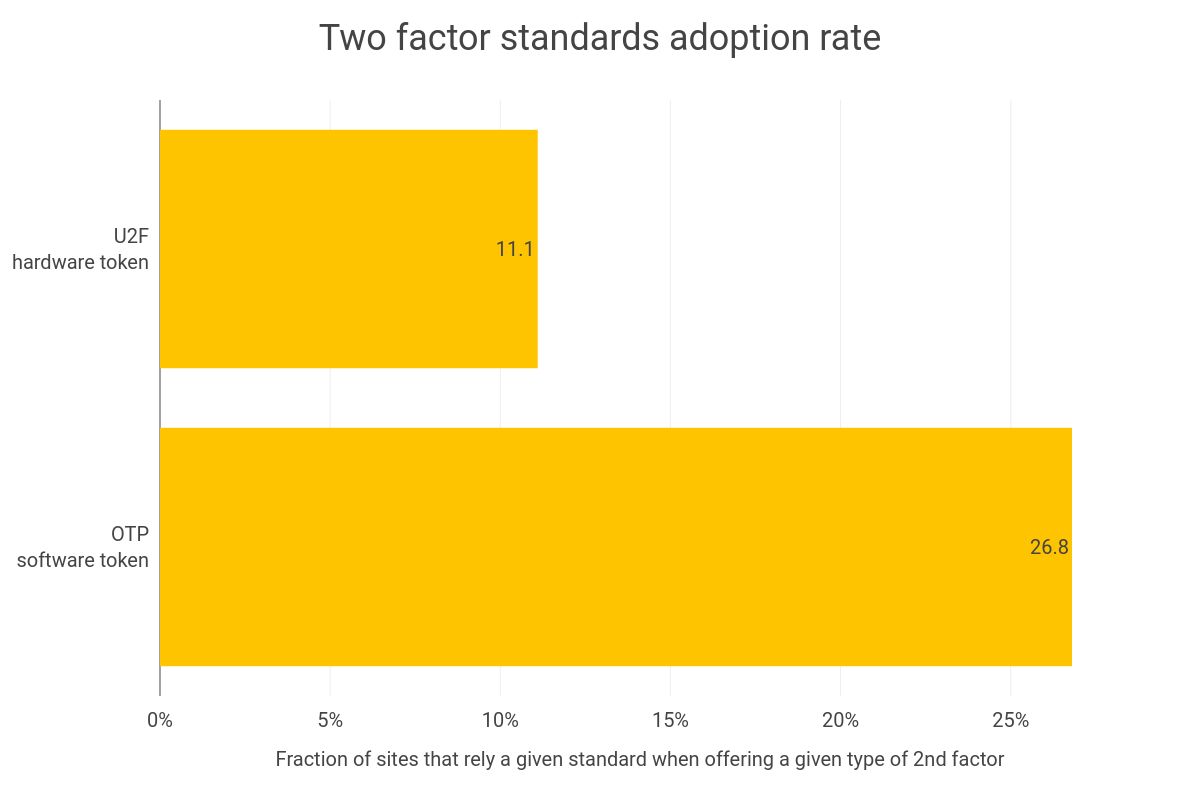
Having reusable two-factors tokens/apps and an Internet-wide consistent experience is only possible if sites adopt standards - this is why measuring adoption prevalence and tracking is so important. As you can see in the figure above, the current plot adoption rate of standards across the industry is pretty bleak - only 11% of the hardware tokens follow the U2F/FIDO standard and 26.8% of the TOTP one.
While the lack of U2F support can be explained by the fact that it is relatively new and was not supported by all major browsers, the lack of support for TOTP is more concerning. The protocol has been around for close to a decade, there are countless apps on Android and OSX that support it, yet barely one in four sites support it. This shows the resistance of the industry to adopt standards, and, thus, calls for a large community effort to get sites to adopt the standard.
Language disparity
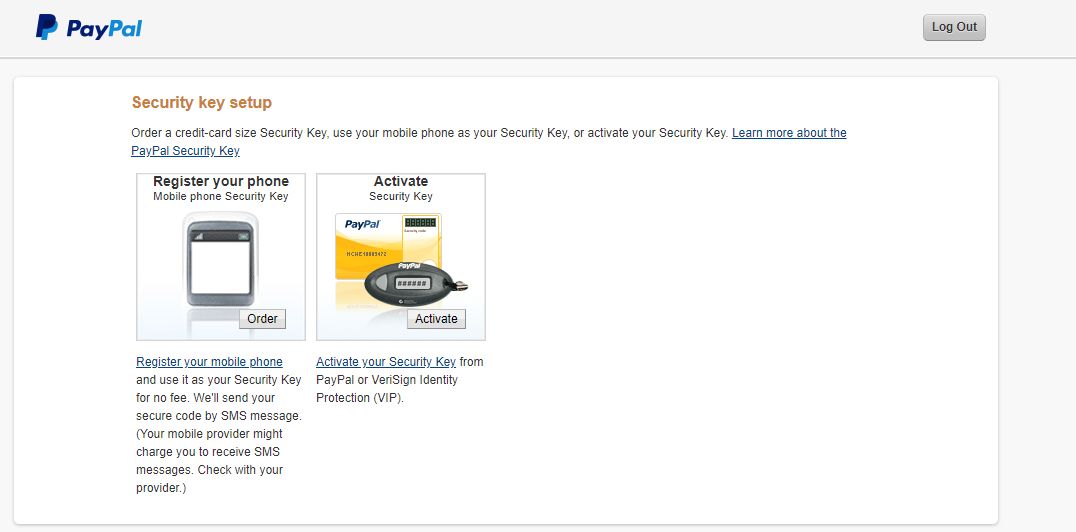
As pointed out by my friend Brad on top of not using standards, many websites use their own made-up language, which further increases user confusion about what to do for security. For example, as visible above, Paypal talk about registering the phone as security keys when it is in reality a SMS system. Twitter call 2FA login verification and Bank of America branded it SafePass and copyrighted the word… For more examples checkout the EFF article on the subject.
Adoption by industry
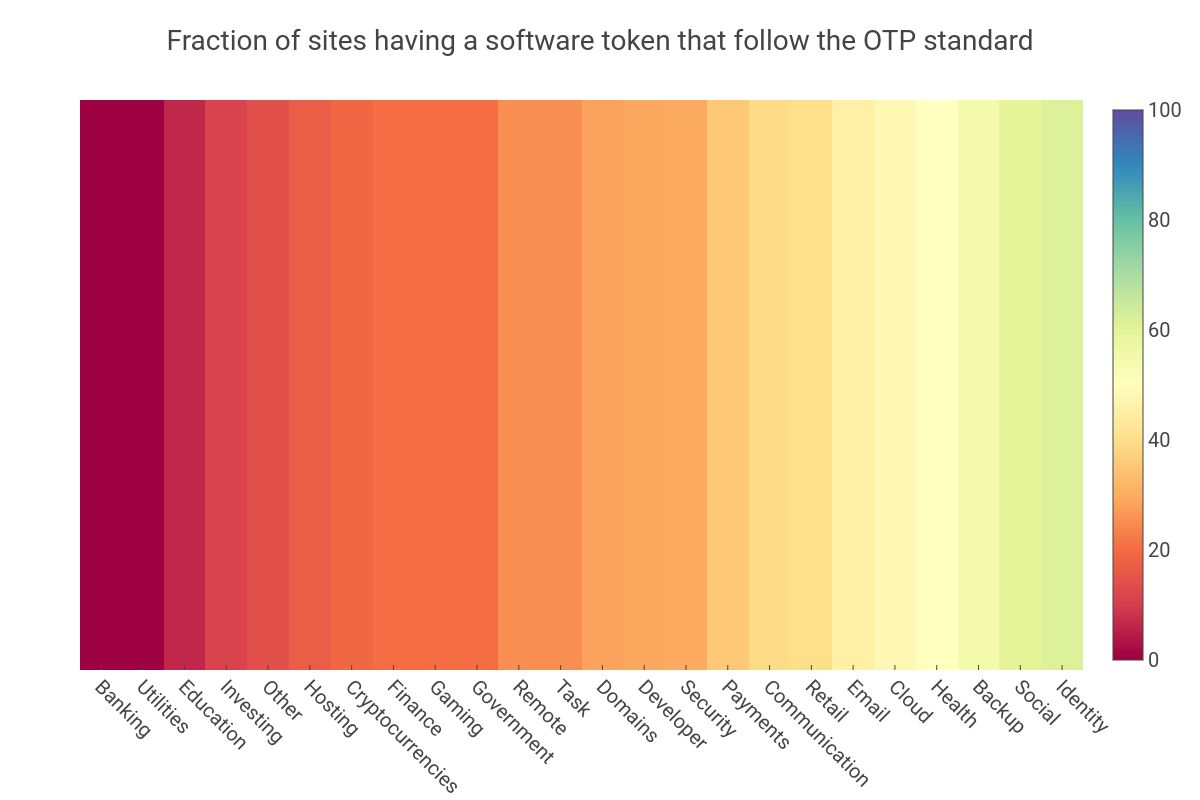
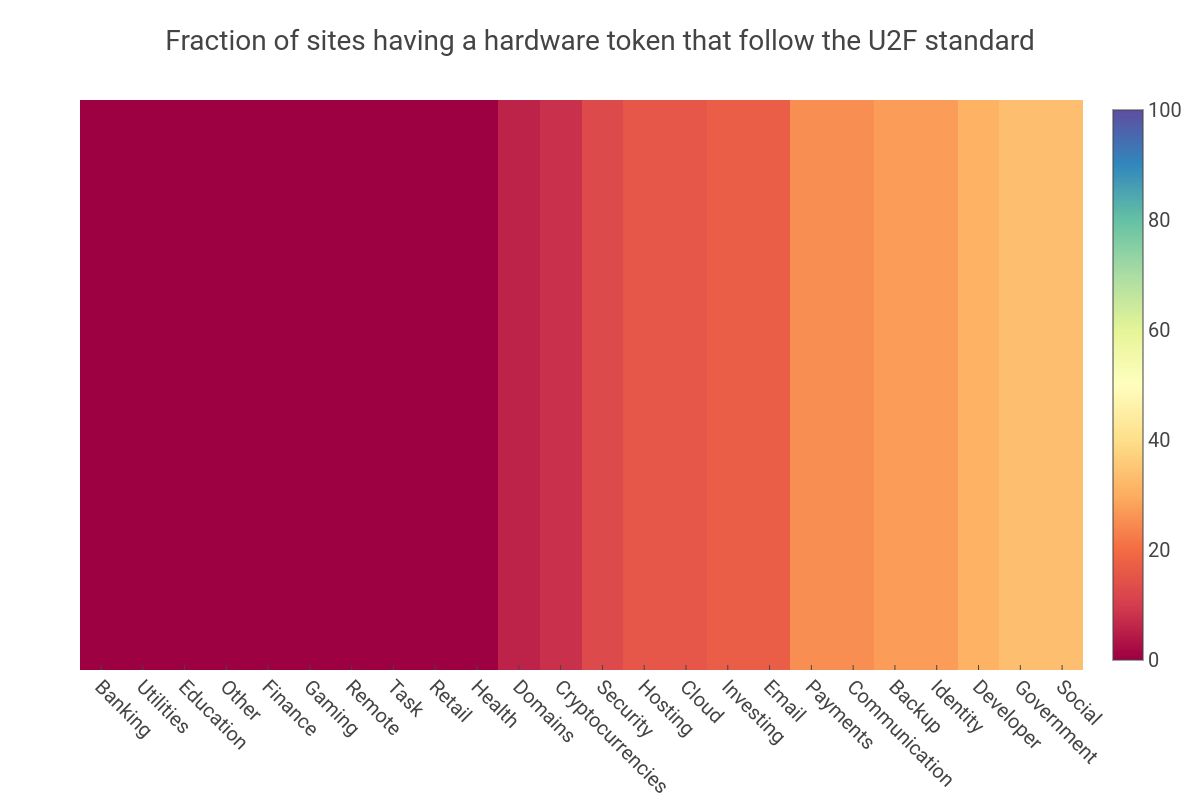
Breaking down the HOTP/TOTP support by industry-type reveals that industries that predate the internet era are the ones that are the least likely to adopt the standards. This raises the question of how the security community can engage with those industries and encourage them to participate in 2FA standardization. The chart below shows that problems with the adoption rate for the U2F standard is as pervasive and suffer the same lack of support that HOTP/TOTP.
Wrap-up
To conclude, we are finally reaching the point where we have the technologies to offer users unphishable accounts with minimal friction and a consistent native UI across the Internet. It is up to us, as a community, to make sure that this doesn’t take 15 years to do, just like the deployment of HTTPS did. We need to engage the industry as a whole and get as many sites as possible, as quickly as possible, on the bandwagon to create a virtuous self-reinforcing circle, instead of a fragmented ecosystem.
A big thanks to Alexei, Aude, Brad and Christiaan for their feedback and insights — this post wouldn’t be half as good without them.
Thank you for reading this blog post till the end! Don’t forget to share it, so your friends and colleagues can also learn about two factor authentication adoption in the wild. To get notified when my next post is online, follow me on Twitter, Facebook or LinkedIn. You can also get the full posts directly in your inbox by subscribing to the mailing list or via RSS.
A bientôt!




