In this post, we analyze how the accessories designed to conceal the use of high-end poker cheating devices in real games work.
This post is the second of my series about high-end poker cheating devices. The first one analyzed how poker cheating devices work and the last one will be about how to defend against such devices. If you haven’t read it yet, please take a moment to do so as this post builds on it.
Alternatively, you can watch our Defcon talk on the subject to get up to speed:
While the cheating device does all the hard work needed to read marked cards remotely and automatically, it can’t be used as a standalone system during a real poker game as the cheating will be too obvious.
For example not only a cheater can’t have their “phone” reading out loud who will win the hand but it is unlikely they will even be allowed to have their phone on the table which is needed to read the cards marking. This is why the manufacturer of cheating devices offer the option to buy small concealed wireless cameras that can be used instead of the integrated camera.
In this post, after discussing the different types of accessory available, we will analyze each type to expose how they operate.
Types of accessories
The poker cheating device comes with three types of accessories:
- Remote control: Used to discreetly change the device settings during a game.
- Wireless cameras: Very compact and hard to spot, the wireless cameras come in many shapes, such as a fake car key or a watch. They are designed to make the cheating harder to spot as the device does not need to be sitting on the table.
- Communication devices: A set of items, including an audio earpiece, that allow the device to tell the cheater covertly which cards were dealt and who has the best hand.
Remote control

Every time a player joins or leaves the poker table, the device settings must be adjusted so the device knows how many hands will be dealt. Of course, continually adjusting the game parameters by fiddling with the “phone” directly would be suspicious. This is why it is shipped with a remote control, showcased in the photo above, which allows the cheater to discreetly change the number of players and ask for the prediction to be repeated.

Analyzing the communication between the remote and the device with a GNU radio and BladeRF reveals than the communication protocol is a simple 2-FSK modulation on the 850-900 MHz ISM band. It is a fairly simple protocol with only three distinct packets (add players, remove players, and repeat analysis).
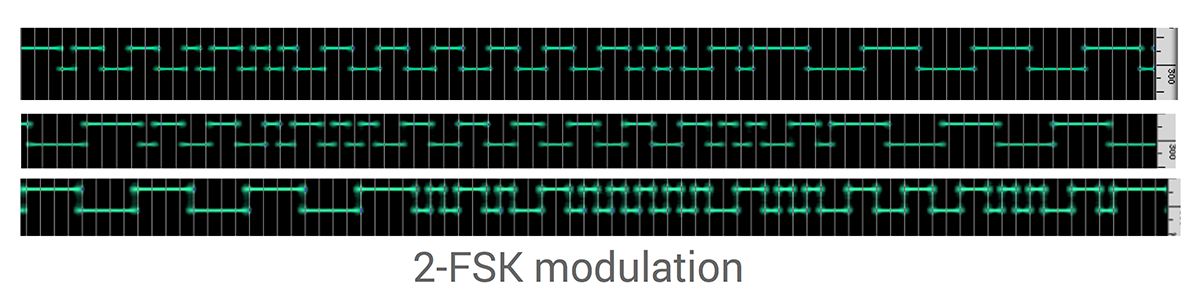
A decoded transmission of these three packets is depicted in the screenshot above. On the device side, the radio signal is handled by the custom communication chip that was added for cheating, as discussed in the previous post.
In terms of security, we observe no randomization or encryption, which makes those packets easily detectable and spoofable. There is not even any type of data whitening. How to exploit this lack of security will be discussed in the next post.
Remote Camera

While to the uninitiated the poker cheating device appears as a regular Android phone, it may still not be practical to keep it on the table, as to do so would not be allowed in most games. To deal with this problem, the creators of the poker device have created a wide range of remote cameras that are hidden in what appear to be innocuous objects. Among others, they offer remote cameras hidden in a belt, watches, a shirt, an ashtray and car keys.

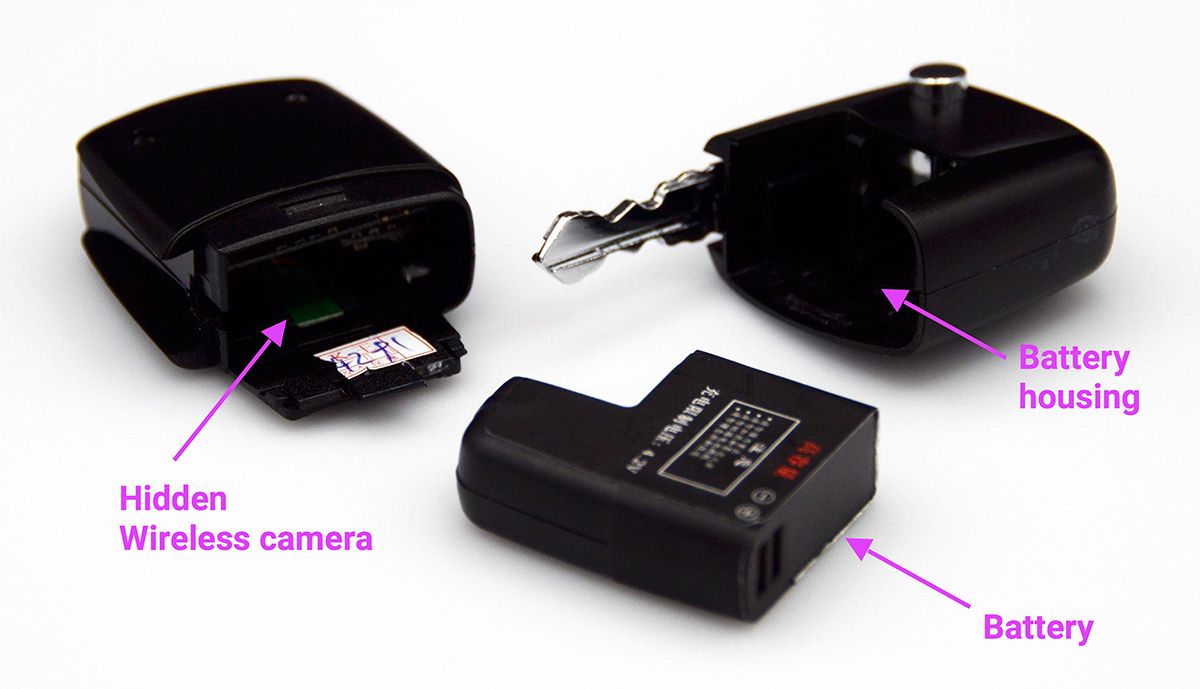
To understand how those remote cameras operate, we acquired a remote camera hidden in a fake car key, which is showcased in the picture above. I went for the car key fob because it seemed the easiest one to tear apart for analysis.
Cleverly, you simply use the close and open door buttons to turn the camera on or off. Here is a short demo of the camera in action to show you how small and realistic it is:
Opening the car key fob reveals, as exposed in the photo below, that the upper part is used to store the battery and the lower side is used to house the hidden camera.
Like the device itself, the shell of the key fob is made of plastic that is meant to let infrared through while still appearing solid. You can see below that under normal lighting, the device appears solid whereas taking a picture in the dark reveals the two infrared LEDs.


Tearing the key fob apart reveals the camera and a LED on one side of the circuit board and the transmission module and the other LED on the other:
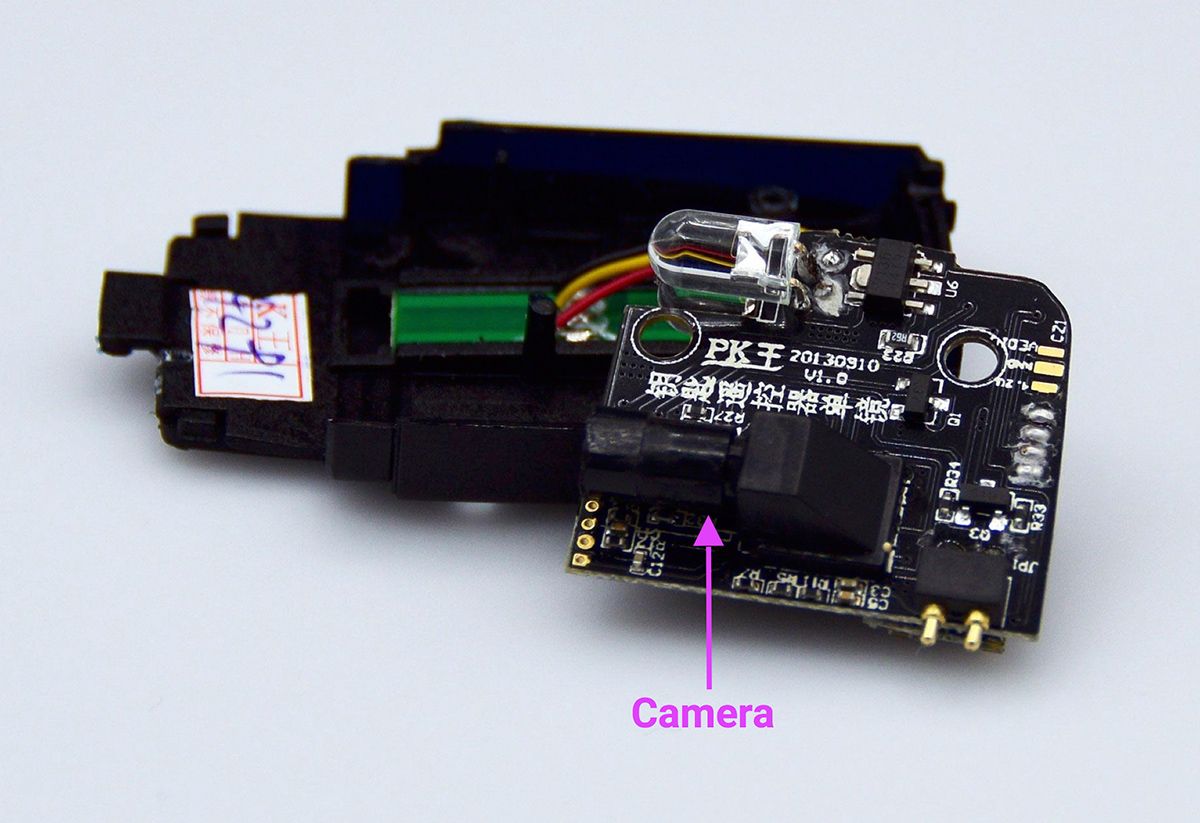
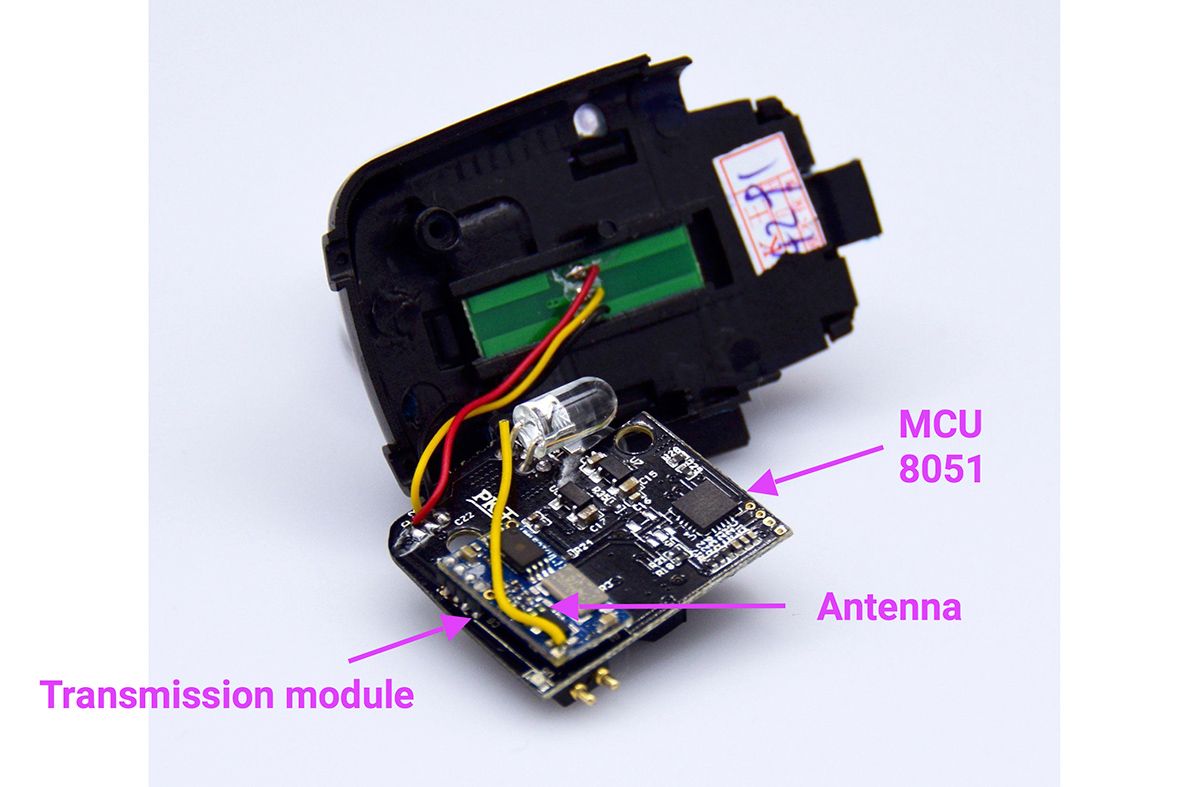
Like for the remote control, we used a BladeRF and GNU radio to understand how the camera communicates with the device. Our analysis reveals that the video is transmitted as an analog stream on the 2.57GHZ band. Here is a spectrogram of the feed as seen by the GNU radio:
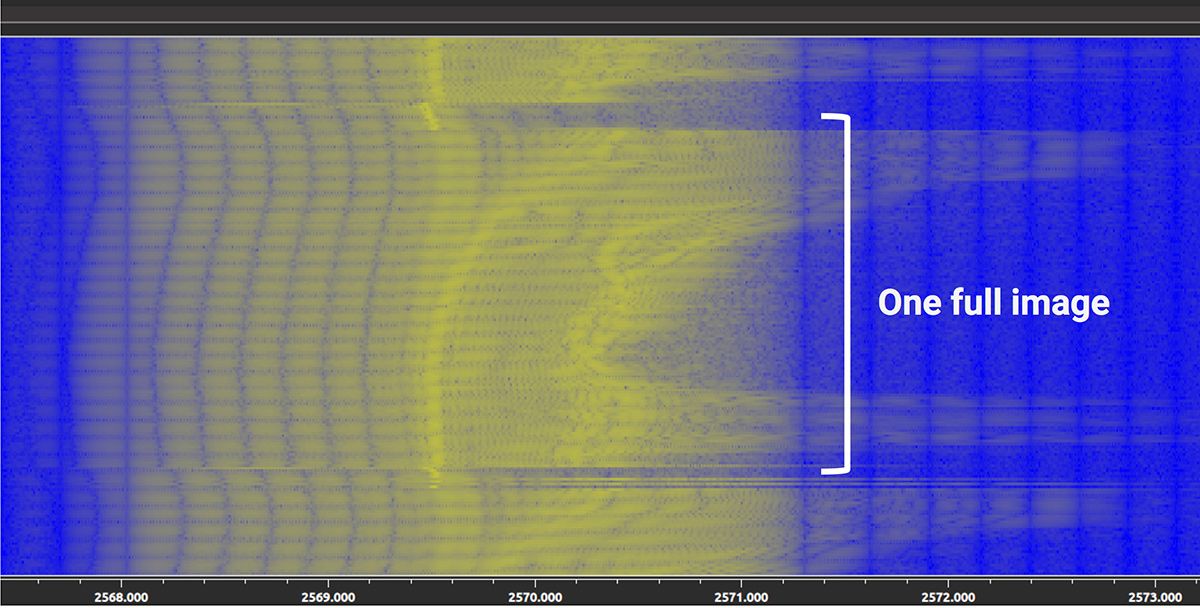
Having an analog feed was a big surprise for us, as we expected some sort of digital encoding in this day and age. However, it seems that simplicity was the main factor when the device was designed and using an analog protocol (like the TVs of ancient times) may be because it allows the device to treat the incoming stream in the same way as the local camera.
In terms of security, the analog signal has, of course nothing that stops us from manipulating and jamming it for detection and defense.
One thing that can’t be conveyed by the photos is that the key runs pretty hot during use. This is not surprising given that the two LEDs run nonstop and the amount of power invested in blasting the video stream. There is clearly room for improvement there, including having the LEDs blink to avoid wasting that much energy. As a result, the key fob doesn’t last long (30 minutes tops), which is why it is shipped with two batteries.
Communication devices
The device comes with two kinds of communication accessories that are designed to communicate covertly with the cheater which player has the best hand. The first is an audio accessory and the second a haptic one. Let’s review them in turn.
Earpiece


The earpiece is a tiny, tiny one as visible on the photo above. It is powered by the smallest radio button I have ever seen in my life. What makes this accessory unique is the way it communicates with the device.
It is way too tiny and underpowered to communicate over Bluetooth, so the device creator opted to use a “bridge” that communicates with the device via Bluetooth and via RF to the earpiece.
This brute-force approach has dire security consequences: while it would have been very hard to detect and tamper with the earpiece over Bluetooth, the RF part makes it trivial, as there is no security whatsoever :-)
Haptic device

Last but not least, the device is shipped with the haptic device showcased in the photo above. This device offers a very sneaky way to communicate with the cheater: it will vibrate one of the mini-vibrators in the order of the strength of the players’ hands. For example, if player 2 has the best hand followed by player 4, then the vibrator labeled 2 will vibrate first followed by the vibrator labeled 4.
In terms of security, because this device communicates over Bluetooth, detecting this device is non-trivial and requires a specific device. Tampering with the communications is even harder and is only possible in specific settings.
This wraps up our tour of the accessories that interact with the poker cheating device. While they are very sophisticated in nature, their communication protocols are a patchwork of technologies that were thrown together as fast as possible to make it work without any thought given to security or efficiency.
The next blog post will discuss how to defend against such devices and exploit their security oversights to jam or disable them. We are still testing a few things and expect this post to be ready sometime in December 2016.
Thanks for reading this post to the end! If you enjoyed it, don’t forget to share it on your favorite social network so your friends and colleagues can too.
To get notified when the next post is online, follow me on Twitter, Facebook, Google+. You can also get the full posts directly in your inbox by subscribing to the mailing list or the RSS feed.




