Big data weaponization and malware-based espionage are usually associated with governments; however, they dont own a monopoly on such activities. Also, online poker uses big data to profile user behavior. Players search for fish (bad players) and they use malware to spy on and rip off infected players at the (online) poker table. This blog post is a brief tour of some of the darkest aspects of online poker. It all started with most online poker sites making a wealth of information about players and the games played readily available to (almost) anyone. Soon a few companies realized that this data could be weaponized to create behavioral profiles and these could be sold to tech savvy players eager to get any edge they can. Later, criminals realized that those players were greedy and therefore offered them a hacked version of the software with a spying module, which was a great and sure way to con money out of them. This blog post explores this dark side of the poker world by looking first at the data available, the software built on it and finally the backdoor version of such software used by poker-playing criminals to spy on other poker players.
A wealth of data
For example, Poker Pro Lab one of the leader in the market offers as a basic tool a database that provides a wealth of information about each person who has ever played on a major website, such as what their win rate is, how many games they have played, among other things.
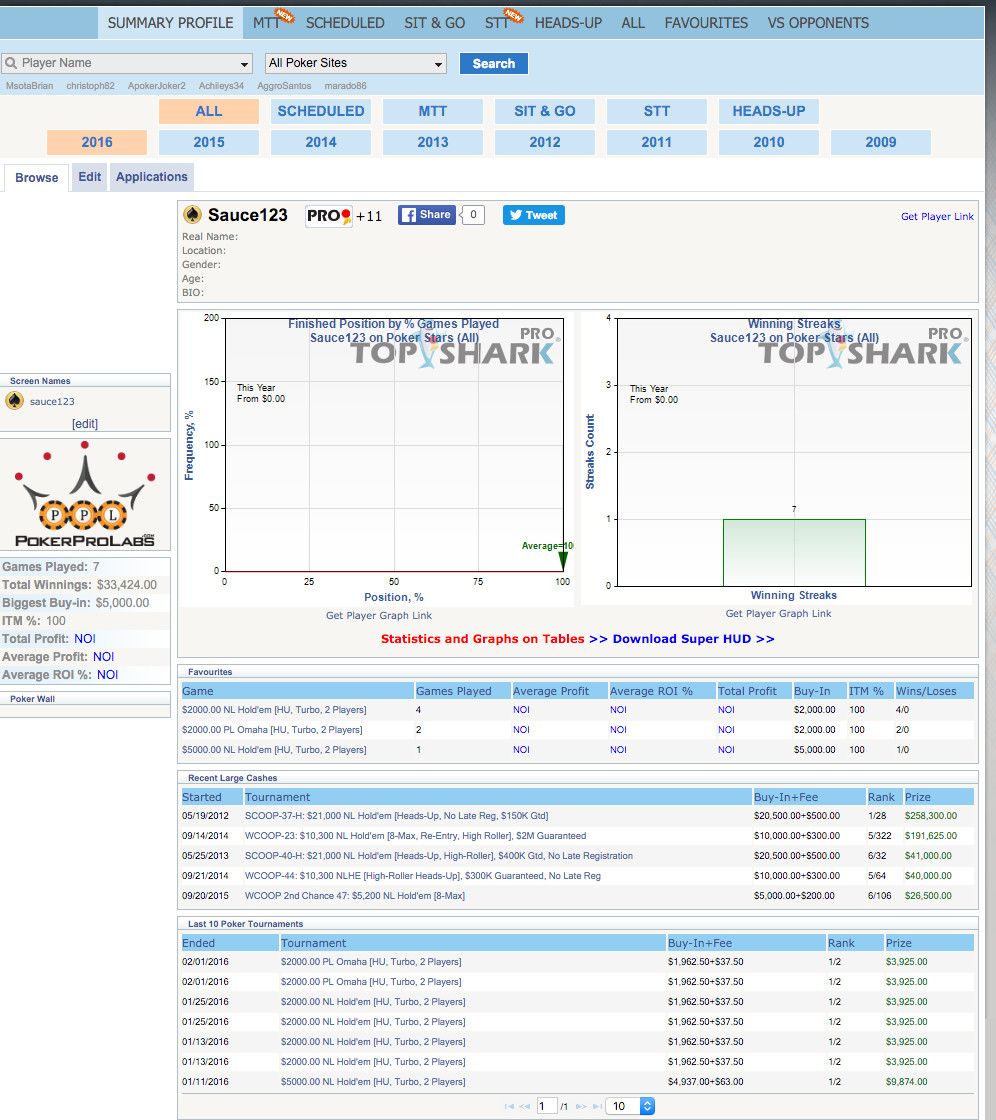
Each poker player has a profile page that can be consulted from their website that summarizes his poker life. For example, as visible in the screenshot above, vicenfish, a famous player, has impressive statistics. We note that some of this information, like ROI, is opt-in to comply with poker sites terms of service. On top of the statistics, the site also provides for each player a rating based on their past performance. As we will see later, this rating is used to help software users to target weaker players at the poker table.
Poker data weaponization
While having a database of statistics is pretty common for most sports, things gets a little more iffy when you realize that these big data sets have been weaponized in software that annotates in real time the most popular poker game sites with their statistics and behavioral profiles. This information, as illustrated below, is meant to help the software users to target the weakest players or exploit a players game pattern to maximize their win rate.
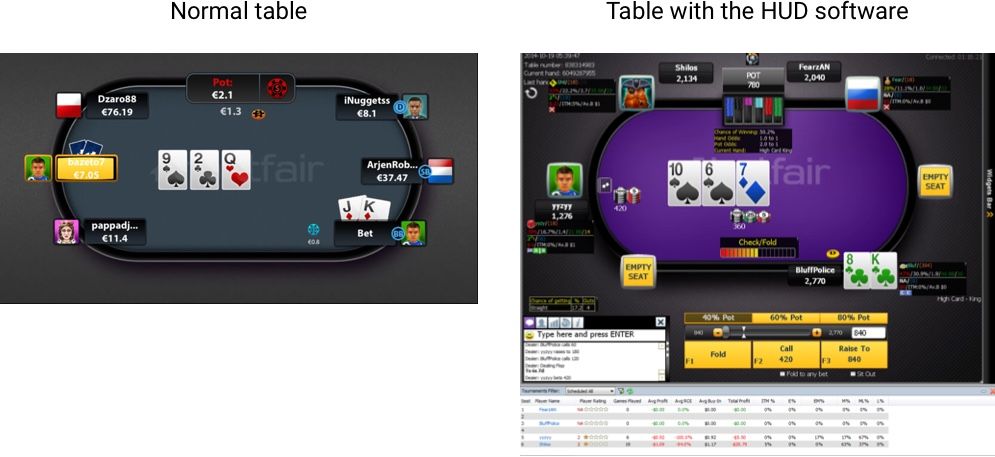
The screenshot above shows you the difference between the table when you use the normal client of a famous site (left) versus what you see when the Super HUD software is running (right). The Super HUD is the software sold by Pro Poker Lab, other exist and are similar. As you can see, there is quite a lot of additional information displayed. Lets briefly look at some of the key features added by the software.
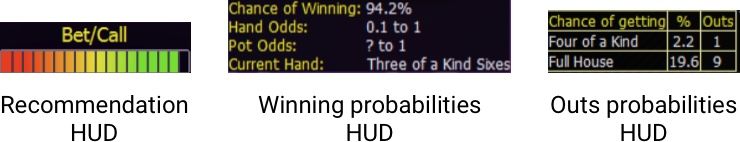
The first one, while not directly related to user profiling, is the odds calculators, which recommend to a player to either keep going or fold. Three of them are visible in the screenshot. The first displays your chance of winning, the second is a meter that makes the information more visual and the third tells you the probability of your hand getting better with the flop, turn and river.
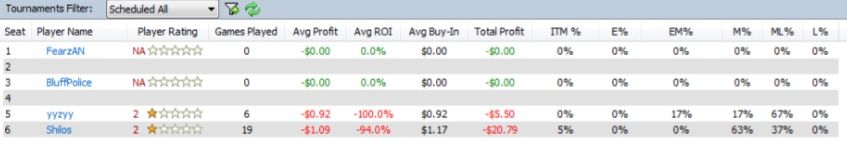
The first place where player behavioral data is used is the statistics panel at the bottom. This panel shows almost the same data that we had in the database:
-
Player rating: This is the same as we saw above. It indicates the strength of the player.
-
Avg Profit and Avg ROI: These give an indication of whether the player is losing or making money at poker. Obviously, people target people who lose.
-
ITM% (in the money percentage): This is how often the player recouped the cost of participating in a tournament by ranking high enough to earn money.
-
E%, EM%, M%, ML%, L%: These summarize how often the player reached a given stage of poker tournaments. For example E% is the percentage of early exits, M% is the percentage of middle-stage exits (top 6080%), ML% is the percentage of the top 1030% exits, and L% is the percentage of finishes in the top 10%.
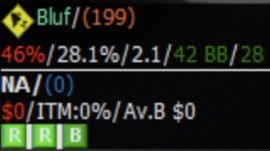
However, the place where behavioral data is truly weaponized is the info box located next to the player portrait, in particular, the icon on the first line as visible in the screenshot above. This icon is based on a behavioral analysis of the players history designed to characterizes their playing style. It indicates whether they are a good mark and the best strategy to beat them. Showing is better than telling, so here a screenshot from the software manual that summarizes all the potential icons:
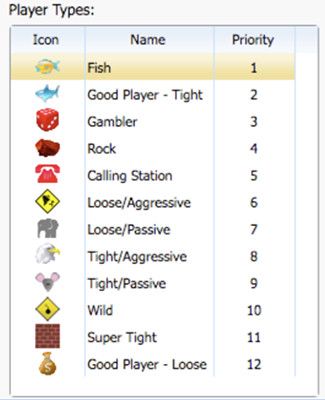
The priority column is meant to inform the users which players they should target to maximize their earnings.
Spying on opponents
A group of hackers took surveillance to the next level by creating a malicious version of this profiling software. It uploaded a screenshot of the victims screen as soon as they connected to a large poker site. The hackers then found the table where the infected player was sitting and ripped them off easily, as they knew exactly which hand they were holding. Investigating this malware (codemame Odlanor) reveals that it was distributed by a phishing site that mimicked a famous poker site. Victims are likely being drawn to this site via emails or some other form of phishing. This specific strain is likely to have become inactive since January 2016, as the site moved and became a parking site. However, it is clear that using malware to earn money at poker is going to endure, given that it makes it easy for bad actors to convert an infection into hard cold cash that can be wired anywhere in the world with little risk of being caught. Readers interested in the technical side of this malware can read the ESET analysis. If you like this post, please share it on your favorite social networks. This helps me to know if my posts are useful and motivates me to keep on writing.




