This blog post shed light on the inner workings of the ransomsphere economics and exposes which cybercriminal groups are the biggest earners.
This is the second blog post in my series about ransomware economics. The first post is dedicated to the methodology and techniques needed to trace ransomware payments end-to-end. As this post builds on that methodology, I encourage you to read through the first post if you haven’t done so. The final post deep-dives into the major ransomware players and analyzes what made them successful.
The findings presented in this post were originally presented at Blackhat USA 2017 in a talk entitled “Tracking desktop ransomware payments end-to-end.” You can get the slides here and a recording of the talk is available on YouTube:
Study limitations
Disclaimer: Before delving into the insights in this post it is important to mention that the numbers reported are undercounting how much money ransomware families are making. This undercounting is due to the fact that we only take into account the bitcoin transactions that we can directly trace back to the ransomware binaries we know of, as explained in the previous blog post about our methodology.
The deliberate choice to only use attributable such transactions was made to ensure that our study is reproducible, which is essential both from a scientific point of view and from the perspective of trustworthiness. All in all this undercounting does not affect the conclusions of the study as we collected enough samples (hundreds of thousands of binaries and transactions) to paint an accurate picture of how the ransomsphere is structured and how much money is flowing into it.
Ransomware is a multi-million dollar business

We have discovered that ransomware is a multi-million dollar business, generating at least 25 million dollars of revenue. This makes ransomware a huge profit center for cybercriminals that is here to stay alongside click-fraud and spamvertisement. Because ransomware authors aggressively leverage other cybercriminal infrastructure (e.g. botnets, exploit kits), this revenue stream benefits the entire black market. If you want to better understand the structure of the black market, read our research paper on the subject.
Ransomware is a a very profitable business that earned cybercriminal over $25 millions in the last few years
Ransomware revenue exploded in 2016
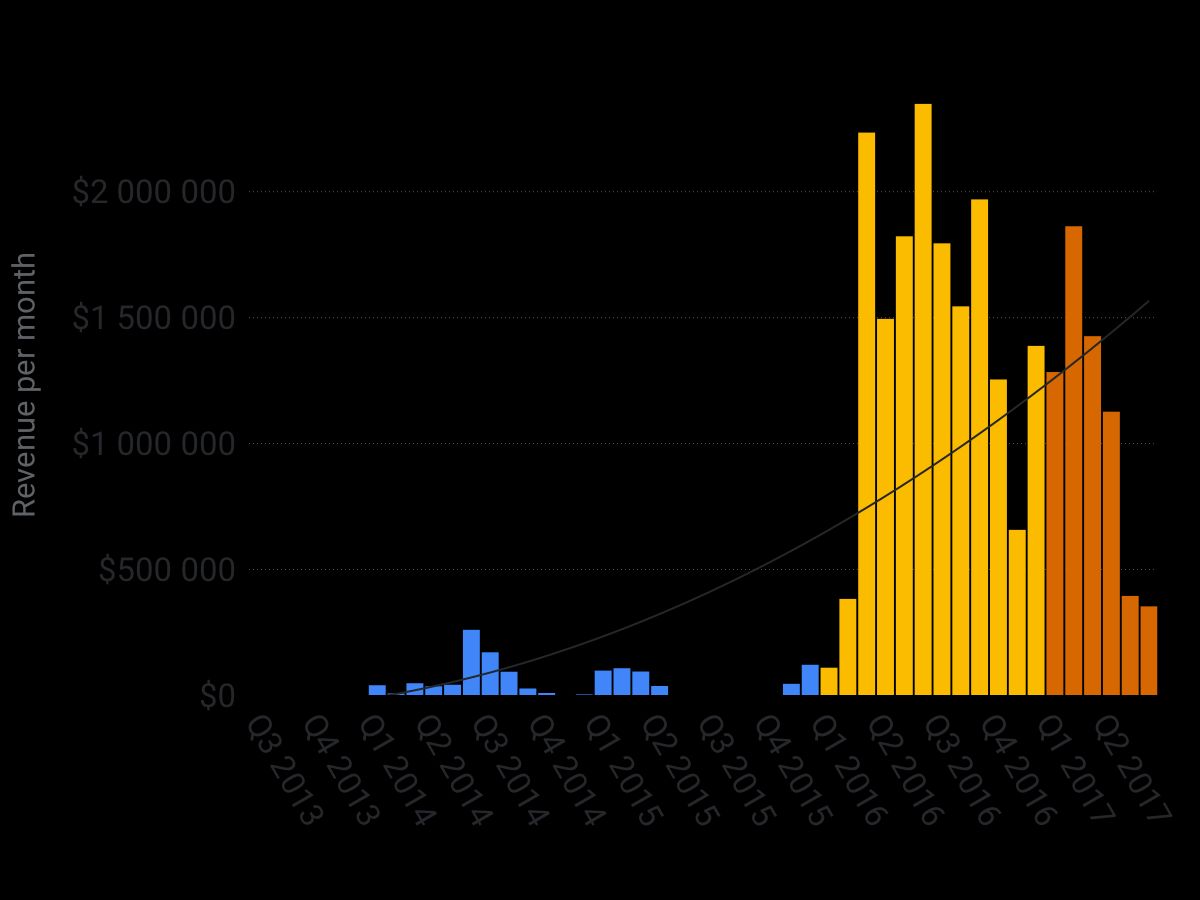
As can be seen in the chart above, which plots ransomware revenue over time, 2016 was a turning point. It was the year ransomware became a multi-million dollar business. This explosive growth is due to many factors including:
- The rise of bitcoin, which made it possible for cybercriminals to cash out large amounts of money.
- Reliance on other cybercriminal infrastructure to widely distribute ransomware binaries. For example, in 2016 Locky used the Necur botnet to scale its spread via spam email campaigns to hundreds of millions of emails daily.
- The growing popularity of employing a ransomware-as-a-service model has resulted in ransomware no longer being a market reserved for tech-savvy cybercriminals.
Ransomware is a very profitable business that earned cybercriminals over $25 millions in the last few years
Ransomware is a winner-take-all market
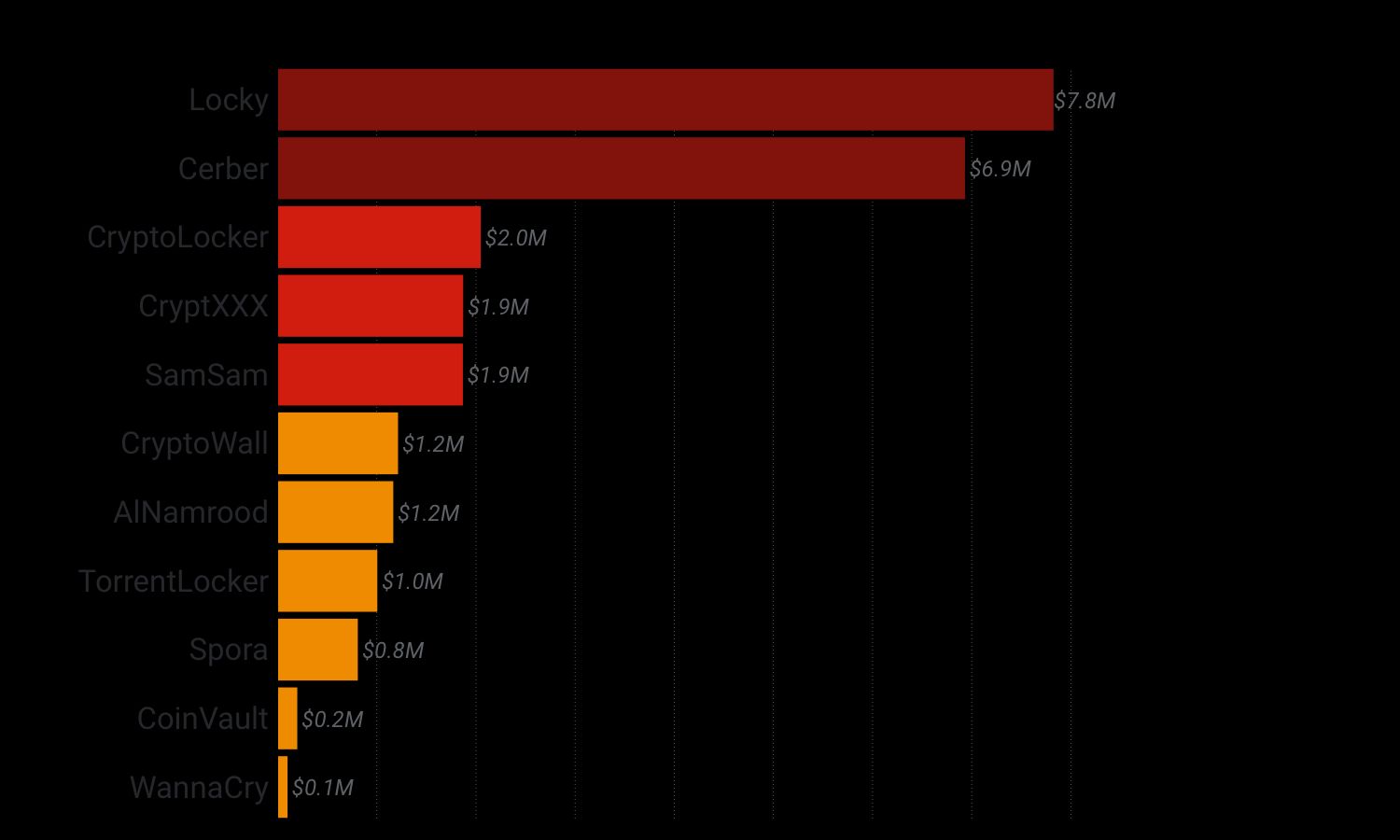
The graph above shows that most of the profit from ransomware is concentrated in only two families: Locky and Cerber. Moreover, only three of the 34 families we traced were able to bring in over a million dollars in revenue, making the ransomware market a winner-take-all market where a few kingpins get rich while the others barely get by. This concentration in the market creates a vicious circle: the more revenue a ransomware author generates, the more it can invest in the means to spread its distribution more widely, which leads to more revenue that they can cash out.
Ransomware is a winner-take-all market dominated by a few kingpins such as Cerber and Locky that made over $5M in the last 2 years.
Ransomware is a fast-changing market
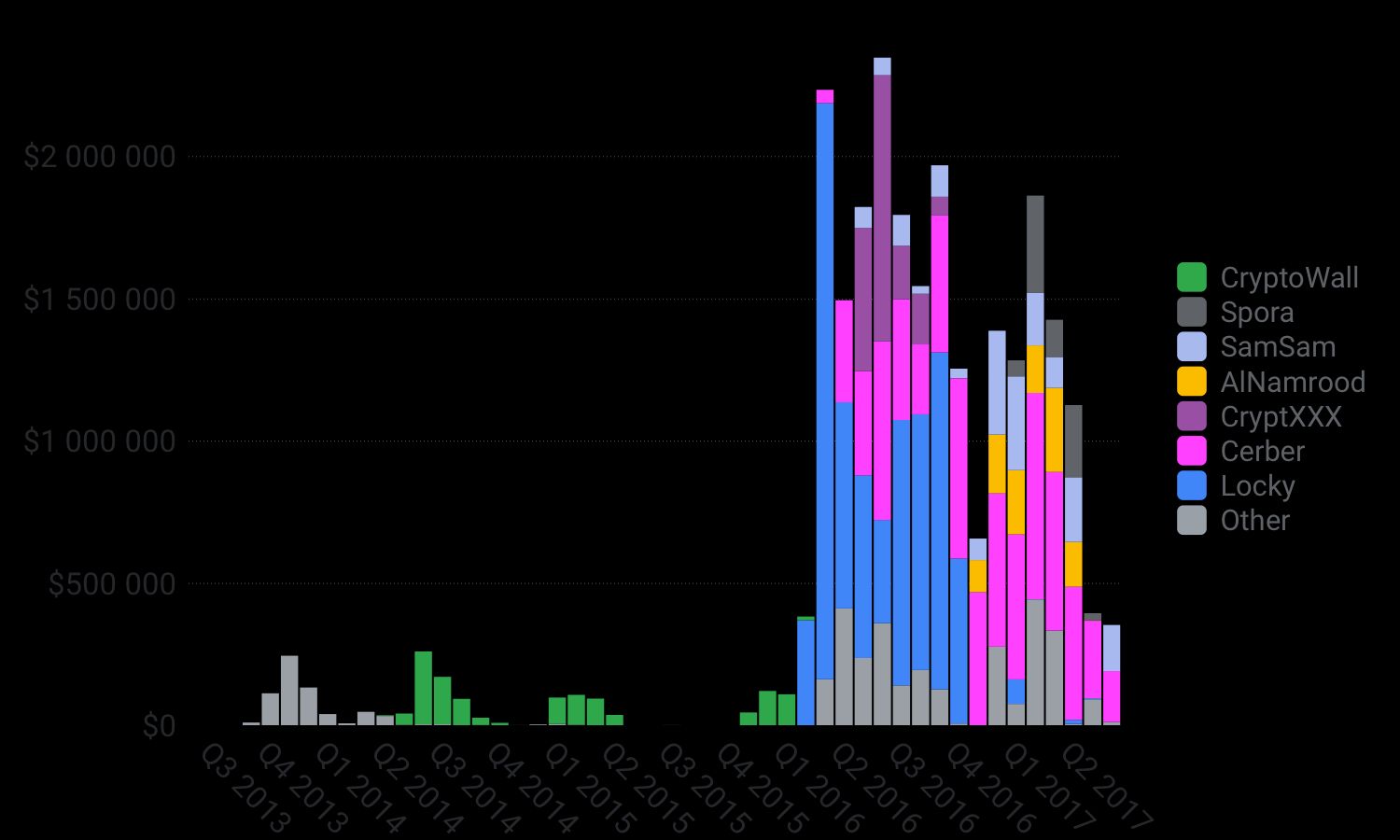
As reported in the chart above that plots revenue over time broken down by ransomware family, the life span of a successful ransomware operation is very short. Even Locky, the arch-dominant ransomware author in 2016, barely lasted a year before being subsumed by Cerber and its affiliate model in 2017. More than ever in 2017, various ransomwares, likely operated by different cybercriminal groups, are fighting for dominance. This intense competition is bad news for users as it pushes criminals to create more sophisticated ransomware.
Most victims buy their bitcoins from their friendly neighbor
Breaking down where victims buy bitcoins reveals that most people favor LocalBitcoins, which allows you to buy bitcoins from someone close by. A few factors potentially explain this behavior:
- It allows victims to pay in cash: this appeals to victims that are embarrassed or don’t trust online brokers.
- The seller can guide them through the payment process: most people aren’t familiar with how bitcoin works so they rely on the seller to help them pay the ransom.
##Bitcoin fee forces people to pay twice

Some ransomware authors, but not all, are very strict on the amount of bitcoin they want in exchange for the key used to decrypt the user’s encrypted files. An unfortunate effect of being strict is that most victims, being unfamiliar with bitcoin, don’t realize that they have to pay a transaction fee. As result, as outlined in the diagram above, we observed that roughly 9% of ransom payments were made in two installments.
BTC-E was the ransomware clearing house
Until 2017, the Russian-based bitcoin exchange BTC-E was the exchange point where almost every ransomware family was cashing out its money. This changed in July 2017, on the same day of our Blackhat USA talk, when the domain was seized by the FBI. It is still unclear as of September 2017 which cashing out point will be favored by ransomware groups next as BTC-E is struggling to get back online.
Wrap-up
As illustrated through this post in the last few years ransoming Internet users has became one of the most profitable cybercriminal activities. Given that people are still not backuping consistently their data and that virtual currency makes ransom payement easier than ever it is only logical to conclude that:
The final blog post of the serie deep-dives into the most successful families and analyze the reasons for their success.
Thank you for reading this post till the end! If you enjoyed it, don’t forget to share it on your favorite social network so that your friends and colleagues can enjoy it too and learn about ransomware.
To get notified when my next post is online, follow me on Twitter, Facebook, Google+, or LinkedIn. You can also get the full posts directly in your inbox by subscribing to the mailing list or via RSS.
A bientôt!




