Theme Selector
Filter by
No Results Found, Please Adjust Your Search

Cybersecurity
DROIDCCT: Cryptographic Compliance Test via Trillion-Scale Measurement
ACSAC 2025

ai
Autonomous Timeline Analysis and Threat Hunting
DEF CON 33 2025
ai
Autonomous Timeline Analysis and Threat Hunting
BH25 2025

AI
Toward Secure & Trustworthy AI: Independent Benchmarking
InCyber Forum 2025

AI
AI for Cybersecurity: Get Started Today
Sectember AI 2024

AI
AI Security: Top 5 Recommendations To Get Started Today
DevFest 2024

user experience
Leveraging Virtual Reality to Enhance Diversity and Inclusion training at Google
CHI 2024
AI
RETSim: Resilient and Efficient Text Similarity
ICLR 2024

AI
Lessons Learned from Developing Secure AI Workflows at Google
RSA 2024

AI
How Large Language Models Are Reshaping the Cybersecurity Landscape
RSA 2024
AI
RETVec: Resilient and Efficient Text Vectorizer
NeurIPS 2023

cybersecurity
How AI helps keeping Gmail inboxes malware free
FIC 2023

cybersecurity
Building Safe End-to-End Encrypted Services for Business - a Google Workspace perspective
RSA 2022

cybersecurity
Who is targeted by email-based phishing and malware? Measuring factors that differentiate risk
IMC 2020

security
Account protections - A Google Perspective
FIC 2020
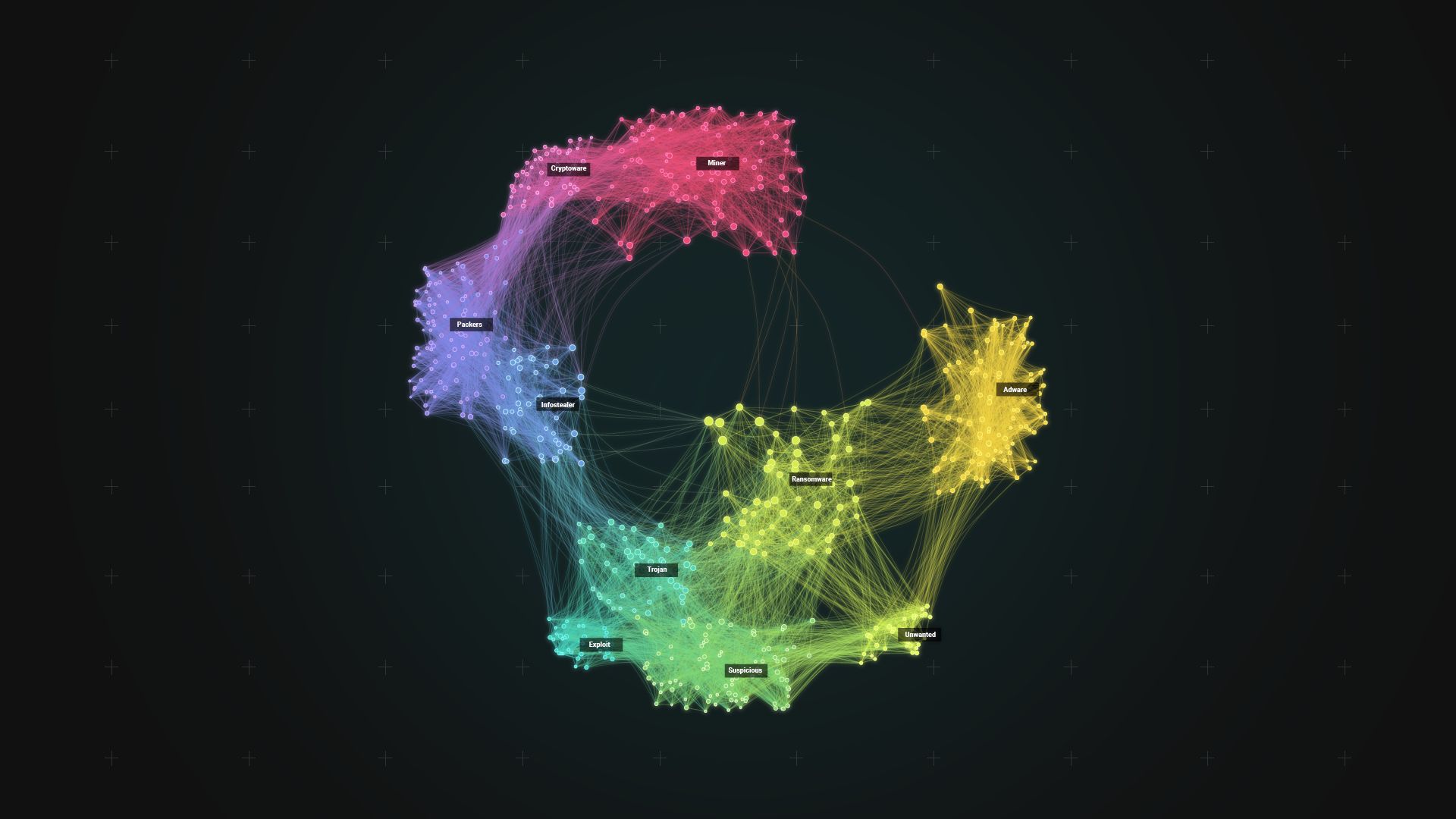
security
Spotlight: Malware Lead Generation At Scale
ACSAC 2020
security
Malicious Documents Emerging Trends: A Gmail Perspective
RSA 2020
web
Insights about the first five years of Right to Be Forgotten requests at Google
Dec 2019
web
Five years of the Right to Be Forgotten
CCS 2019

security
Protecting accounts from credential stuffing with password breach alerting
Usenix Security 2019

anti-abuse
Deconstructing the Phishing Campaigns that Target Gmail Users
Black Hat USA 2019

ai
Cutting Edge TensorFlow - Keras Tuner: hypertuning for humans
IO 2019

security
Password checkup: from 0 to 650, 000 users in 20 days
Mar 2019

ai
Attacks against machine learning — an overview
May 2018

ai
How to handle mistakes while using AI to block attacks
Apr 2018
ai
Challenges faced while training an AI to combat abuse
Apr 2018
ai
Why AI is the key to robust anti-abuse defenses
Apr 2018

ai
How to successfully harness AI to combat fraud and abuse
RSA 2018

network security
Taking down Gooligan part 3 — monetization and clean-up
Mar 2018

network security
Taking down Gooligan: part 2 — inner workings
Mar 2018

network security
Taking down Gooligan: part 1 — overview
Mar 2018

network security
Hunting down Gooligan — retrospective analysis
Botconf 2017

security
Tracking desktop ransomware payments end to end
S&P 2018

anti-abuse
Data Breaches, Phishing, or Malware? Understanding the Risks of Stolen Credentials
CCS 2017
security
Unmasking the ransomware kingpins
Oct 2017

security
Exposing the inner-workings of the ransomware economy
Sep 2017

security
How to trace ransomware payments end-to-end - an overview
Aug 2017

security
Tracking ransomware payments end to end
BH USA 2017

anti-abuse
Pinning Down Abuse on Google Maps
WWW 2017

web security
Learn web security with Google
IO 2016

security
Targeted Attack Against Corporate Inboxes A Gmail Perspective
RSA 2017

anti-abuse
Picasso: Lightweight Device Class Fingerprinting for Web Clients
SPSM 2016

anti-abuse
Investigating commercial pay-per-install and the distribution of unwanted software
Usenix Security 2016

web security
How google helps 600,000 webmasters re-secure their hacked sites every year
Jun 2016

anti-abuse
In-depth analysis of the lessons we learned while protecting gmail users
Apr 2016

security
Lessons learned while protecting Gmail
Enigma 2016

network security
How email in transit can be intercepted using dns hijacking
Jan 2016

network security
Understanding how tls downgrade attacks prevent email encryption
Dec 2015
network security
Neither snow nor rain nor mitm . . . an empirical analysis of email delivery security
IMC 2015

anti-abuse
Secrets, lies, and account recovery: lessons from the use of personal knowledge questions at google
WWW 2015

anti-abuse
Ad injection at scale: assessing deceptive advertisement modifications
S&P 2015

anti-abuse
Handcrafted fraud and extortion: manual account hijacking in the wild
IMC 2014

anti-abuse
Dialing back abuse on phone verified accounts
CCS 2014

user experience
Meaning matters: why google switched to numeric captchas
Apr 2014

user experience
Easy does it: more usable captchas
CHI 2014

user experience
Online microsurveys for user experience research
CHI 2014