Theme Selector
Filter by
No Results Found, Please Adjust Your Search

ai
Wingardium Trivia-osa! On-Device Sorting Hatbot Powered by Gemma, Ollama, USearch, and RETSim
May 2024

ai
On the consequences of the AI workforce entering the market
Jun 2023

how-to
Stay safe online in 10 easy steps
Aug 2021

Magic
3 million smiles during the pandemic - the retrospective
Jul 2021

cryptography
Hacker's guide to deep-learning side-channel attacks: code walkthrough
Jun 2021

cryptography
Hacker's guide to deep-learning side-channel attacks: the theory
May 2021
web
Insights about the first five years of Right to Be Forgotten requests at Google
Dec 2019

user experience
Understanding the online safety and privacy challenges faced by South Asian women
Jun 2019

security
Password checkup: from 0 to 650, 000 users in 20 days
Mar 2019

security
Account security - a divided user perception
Feb 2019

security
The bleak picture of two-factor authentication adoption in the wild
Dec 2018

web
Quantifying the impact of the Twitter fake accounts purge - a technical analysis
Aug 2018

ai
Attacks against machine learning — an overview
May 2018

ai
How to handle mistakes while using AI to block attacks
Apr 2018
ai
Challenges faced while training an AI to combat abuse
Apr 2018
ai
Why AI is the key to robust anti-abuse defenses
Apr 2018

network security
Taking down Gooligan part 3 — monetization and clean-up
Mar 2018

network security
Taking down Gooligan: part 2 — inner workings
Mar 2018

network security
Taking down Gooligan: part 1 — overview
Mar 2018

cybersecurity
Inside Mirai the infamous IoT Botnet: A Retrospective Analysis
Dec 2017
security
Unmasking the ransomware kingpins
Oct 2017

security
Exposing the inner-workings of the ransomware economy
Sep 2017

security
How to trace ransomware payments end-to-end - an overview
Aug 2017

privacy
Understanding how people use private browsing
Jul 2017

web security
Understanding the prevalence of web traffic interception
Jun 2017

how-to
Ten simple steps for keeping your laptop secure
Apr 2017

hacking
Bad beat: practical attacks against poker cheating devices
Mar 2017

hacking
Royal flush: an in-depth look at poker cheating devices accessories
Nov 2016

hacking
Full(er) House: Exposing high-end poker cheating devices
Oct 2016

video game
Predicting Hearthstone game outcome with machine learning
Oct 2016

hacking
What are malicious usb keys and how to create a realistic one?
Aug 2016

how-to
5 useful tips to bulletproof your credit cards against identity theft
Jul 2016

web security
How google helps 600,000 webmasters re-secure their hacked sites every year
Jun 2016

hacking
Concerns about usb security are real: 48% of people do plug-in usb drives found in parking lots
Apr 2016

anti-abuse
In-depth analysis of the lessons we learned while protecting gmail users
Apr 2016

web
How an improved responsive design and faster site increased visitor engagement by 104%
Mar 2016

hacking
The dark side of online poker or the commoditization and weaponization of big data and espionage
Feb 2016

hacking
What tools do the fbi use when seizing computers or the curious case of the mouse jiggler device
Jan 2016

network security
How email in transit can be intercepted using dns hijacking
Jan 2016

network security
Understanding how tls downgrade attacks prevent email encryption
Dec 2015

anti-abuse
How phishing works
Aug 2015

video game
Hearthstone 3d card viewer in pure javascript/css3
Apr 2015

web security
19.5% of https sites trigger browser warning as they use sha-1 signed certificates
Jan 2015

video game
I am a legend: Hacking Hearthstone with machine-learning Defcon talk wrap-up
Sep 2014

video game
Predicting a Hearthstone opponent’s deck using machine learning
Aug 2014

video game
Pricing hearthstone cards with unique abilities: VanCleef and The Twilight Drake
Aug 2014

video game
How to find undervalued Hearthstone cards automatically
Jul 2014

video game
How to appraise Hearthstone card values
Jul 2014

web
Choose the right sharing icon to boost user engagement
Jun 2014

privacy
Using big data to understand users' privacy concerns
May 2014

user experience
Meaning matters: why google switched to numeric captchas
Apr 2014

security
Survey: most people don't lock their android phones - but should
Mar 2014

user experience
Phone screen size: bigger isn't always better
Jan 2014

web
High-end macbook pro retina (late 2013, 15in) benchmark
Oct 2013

web
The (untold) price of doing local search
Sep 2013

anti-abuse
When a porn site masquerades as the apple app store
May 2013

web security
Apple finally turns HTTPS on for the app store, fixing a lot of vulnerabilities
Mar 2013

anti-abuse
18.4% of us internet users got at least one of their account compromised
Jan 2013

web security
How we broke the nucaptcha video scheme and what we propose to fix it
Feb 2012

web
Porn domain not that sexy: no rush to have .xxx
Dec 2011

anti-abuse
What phishing sites look like ? (study)
Nov 2011

web security
Evolution of the https lock icon (infographic)
Nov 2011
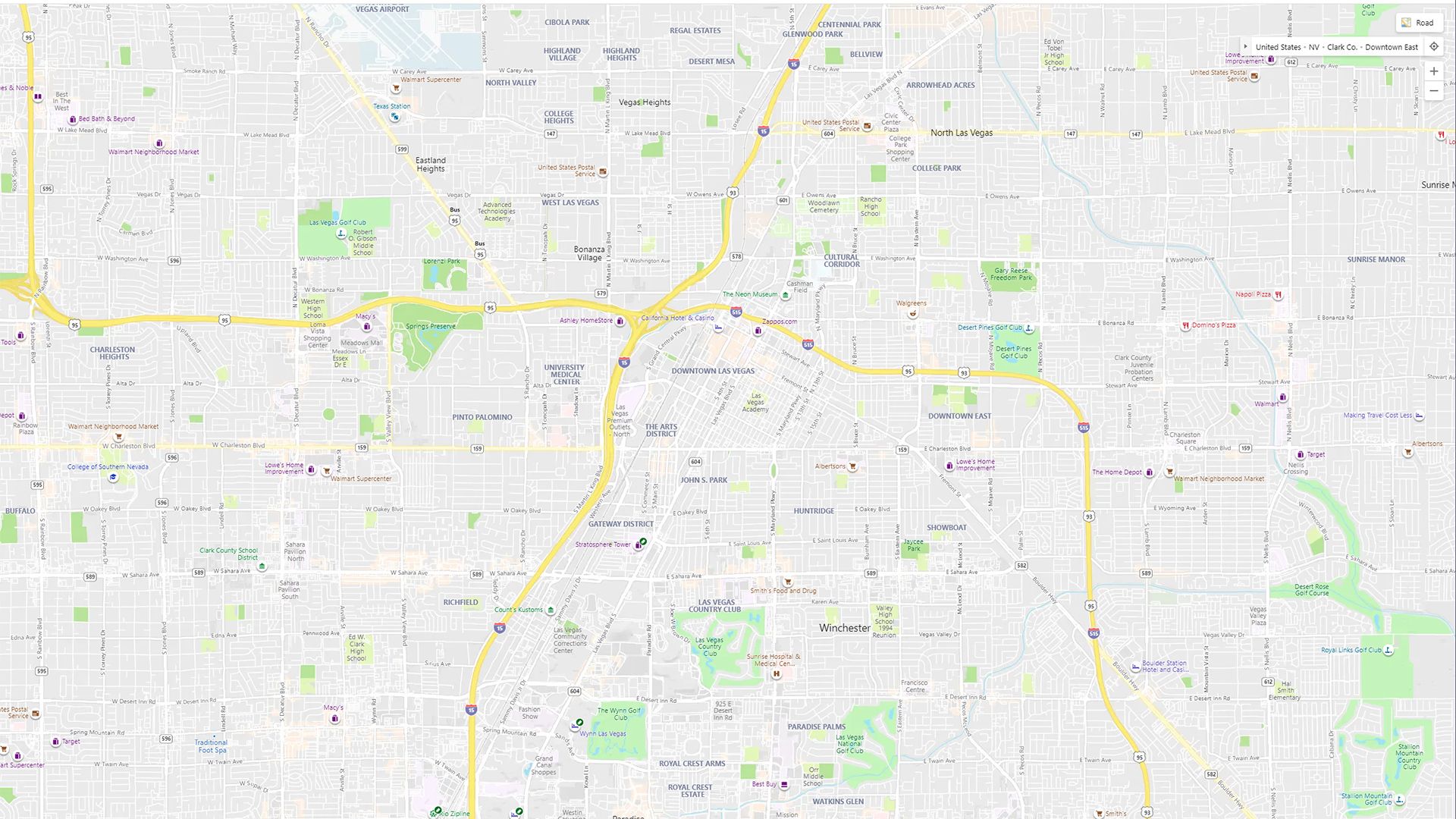
privacy
Using the microsoft geolocalization api to retrace where a windows laptop has been
Jul 2011

web security
Tracking users that block cookies with a http redirect
Jul 2011

web security
Five surprising captcha schemes
Mar 2011

security
Some insights about password shapes
Feb 2011

hacking
Identifying internet explorer user with a smb query
Aug 2010